Agentless, Self Managing
Single on the edge deployment, self managing with automated server side updates. Enables full visibility into attack surface traffic and intent.
Netacea Bot Management
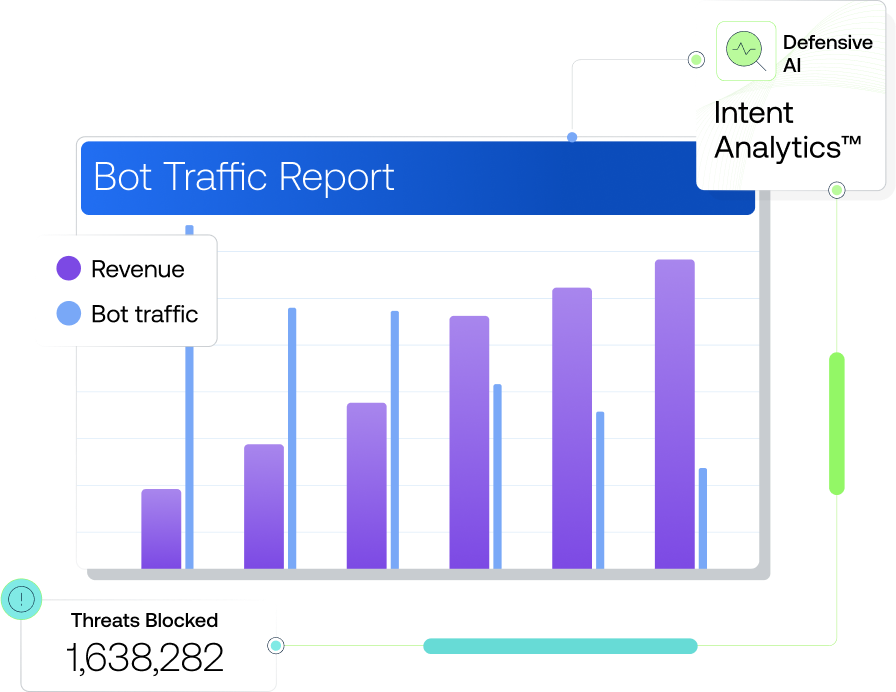
Get visibility into malicious bot traffic across your entire attack surface. Accurately detect attacks and automate your attack response with trusted, industry-leading defensive AI.
Why Netacea
Single on the edge deployment, self managing with automated server side updates. Enables full visibility into attack surface traffic and intent.
Truly autonomous detection and response. Trusted by enterprise SOC teams. Proven to block bots 33x more effectively, with a 0.001% false positive rate.
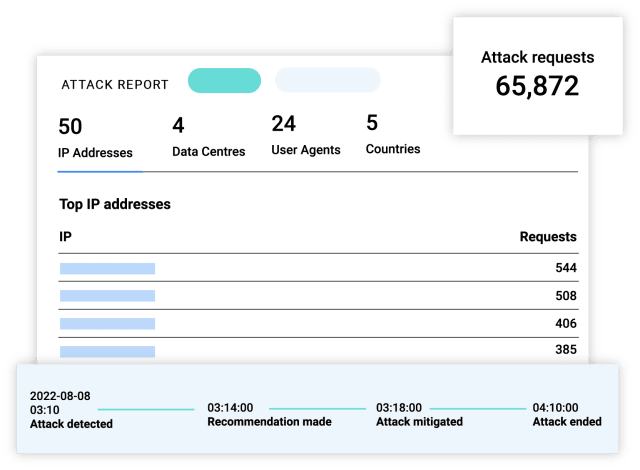
Visualise live attacks as they happen. Understand traffic behavior and enhance strategic and operational decision making.
Existing bot controls are being defeated by bot attacks. Bypassing detection, exploiting gaps, hoarding inventory, scraping IP and committing various forms of automated online fraud. Amounting to a serious cost to your business and customers.
Overcome:
Key Features To Defeat Bots
Our server-side Bot protection scrutinizes user behavior across your Websites, Apps & APIs. This data is then fed into Intent Analytics™, our machine learning engine to identify if it is a automated threat and if immediate action needs to be taken.
Like for like comparisons show Netacea identifies up to 20x more threats whilst maintaining industry leading 0.001% false positives.
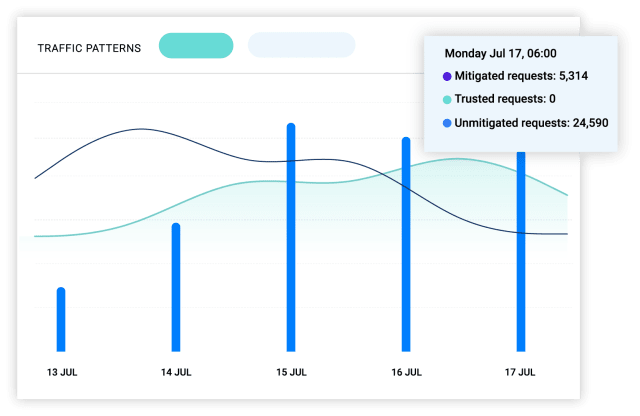
Attackers exploit what they can see. With server side protection from Netacea, your bot protection becomes invisible. Attackers wont know whats blocking them. This costs them money and effort making you an expensive target encouraging them to give up.
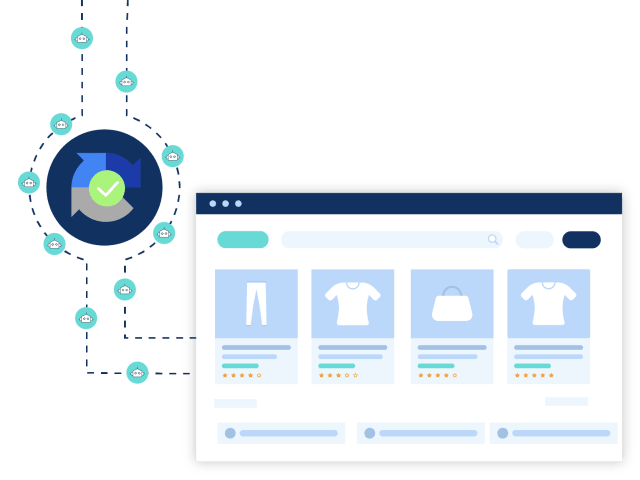
Netacea users benefit from an always ready active threat database that constantly updates and adapts itself to evolving threats without the need to wait for rule changes or manual updates that leave you vulnerable to attacks.
Every time a bot attacks and then retools, Netacea adapts in real time to thwart it. Whilst updating to protect all our customers with the same anti bot intelligence. So your always up to date against the latest threats.
Signature-based tools designed to deal with bots need babysitting to be even a little bit effective. Netacea is hyper light touch to manage with no agents or signature updates required, our solution does it all for you. By automating tasks that were once manual you get better threat prevention, more time back and feel a little less exhausted dealing with bot traffic.
When it’s needed Netacea’s engine is augmented by an expert team of data scientists and industry leading bot threat intelligence experts. They’re there to monitor activity, analyze threats in-depth and scoop up outliers.
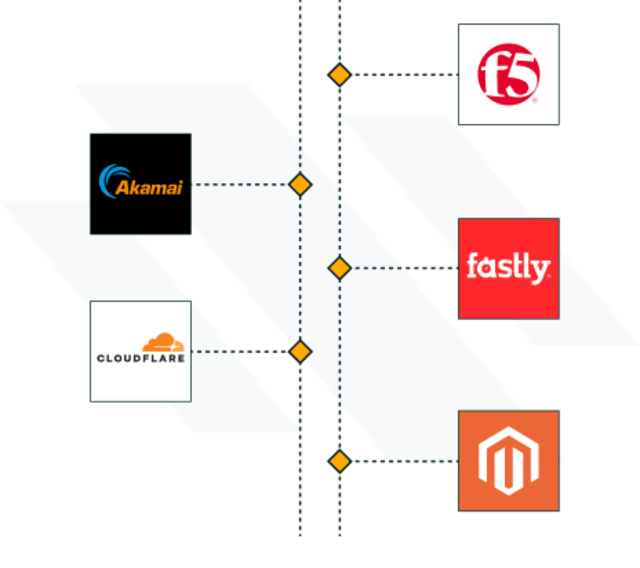
New tech, platforms and complex setups demand anti bot protection that covers you and your customers where you need it. Our cloud based approach allows for rapid deployment, massive scale with integrations for CDNs, load balancers and web platforms. Getting you up and running in minutes.
Stop malicious actors from seizing control of customer accounts.
Detect and block automated card cracking, carding and enumeration attacks.
Stop attackers from brute forcing their way into your customers' accounts.
Halt attempts to create masses of accounts; damaging your business.
Prevent exploitation of new account bonuses and fake account creation.
Maintain the integrity of online sales and ensure goods go to real customers.
Prevent bots from stealing your marketing budget and skewing your analytics.
Identify and stop web scrapers that compromise your website.
Frequently Asked Questions
Experience 33x Better Bot Protection From The Edge.
Netacea bot detection and mitigation software helps you cut costs, secure your attack surface and build brand trust online.
Netacea Bot Protection Customers Are Winning: